%20(1).png)
%20(1).webp)
Better control over access
Take control of access with less effort, letting Veriam handle the hard parts.
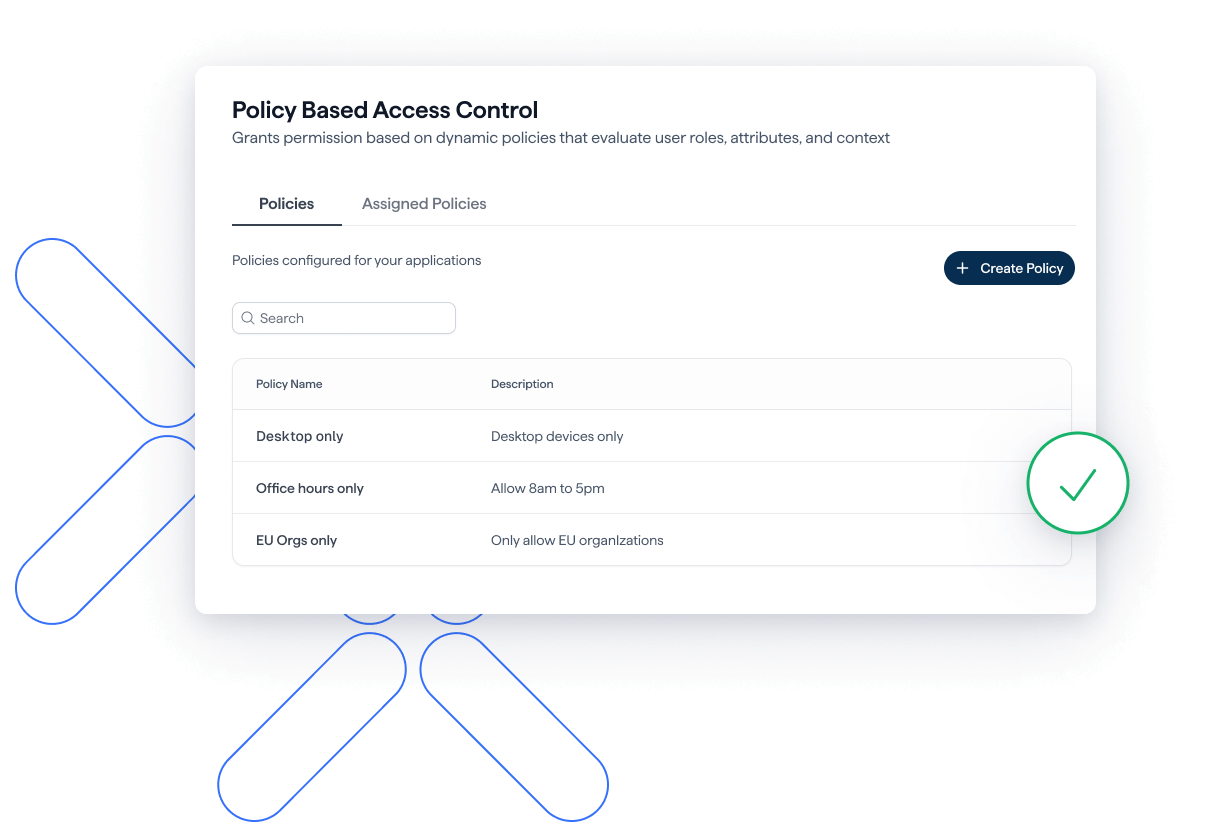
Set rules for who gets access
Use clear policies to decide who gets access to what, with Policy-Based Access Control (PBAC).
- Control access with specific user access conditions.
- Set access based on roles, permissions, resources, and timing.
- Policies make sure only the right people can access data.
- Make your authorization process safe and simple.
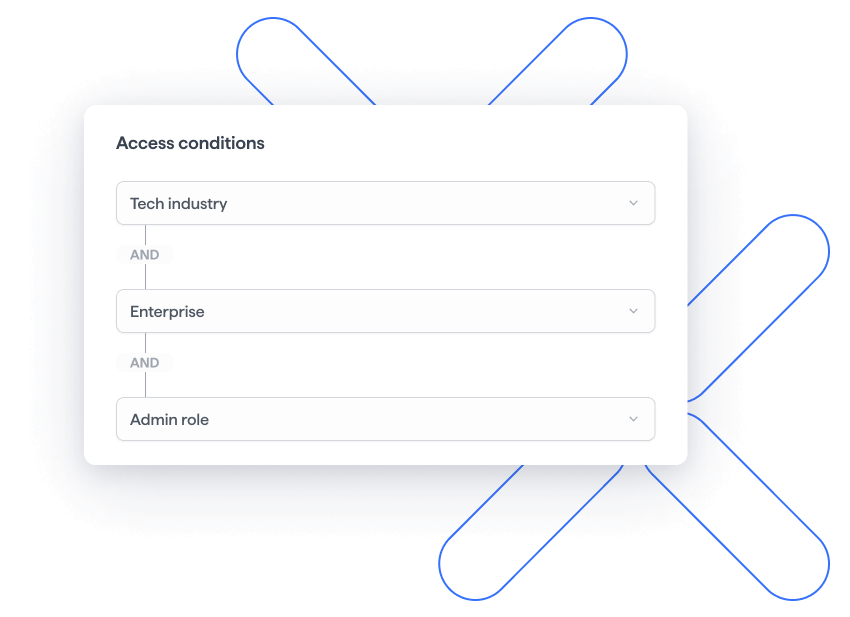
Decide access based on user or customer details
Give access based on user or customer information, with Attribute-Based Access Control (ABAC).
- We check user or customer details to decide access.
- Use roles, affiliations, credentials, and organizational information to manage permissions.
- Access is only given when attributes are verified. Your business is safe and compliant.

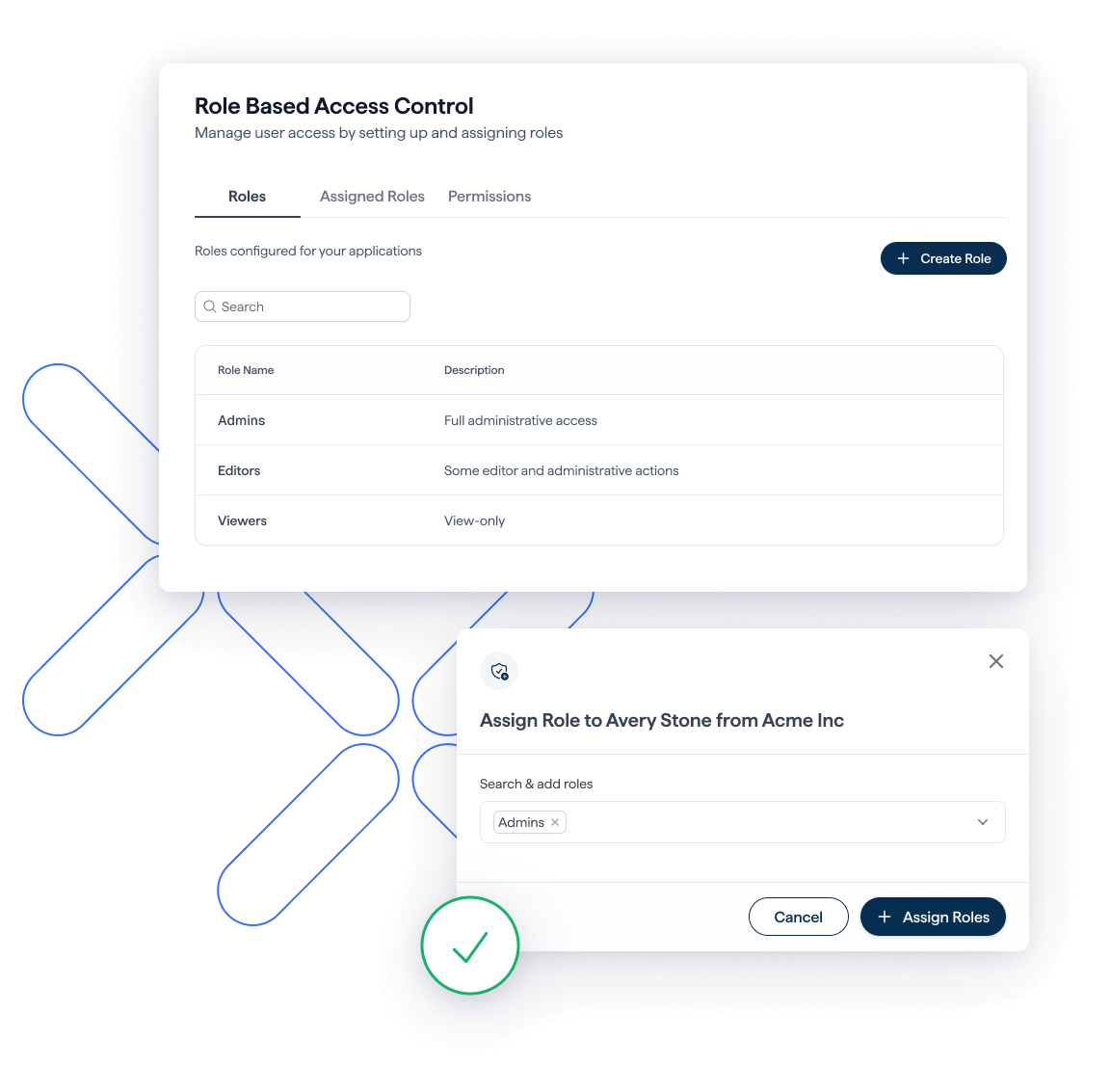
Give access based on roles
Give access and permissions based on user roles, with Role-Based Access Control (RBAC).
- Decide who gets access by assigning user roles.
- Give each role specific permissions and responsibilities.
- Let users complete their tasks effectively and securely.
- RBAC helps avoid mistakes and the wrong people getting in.
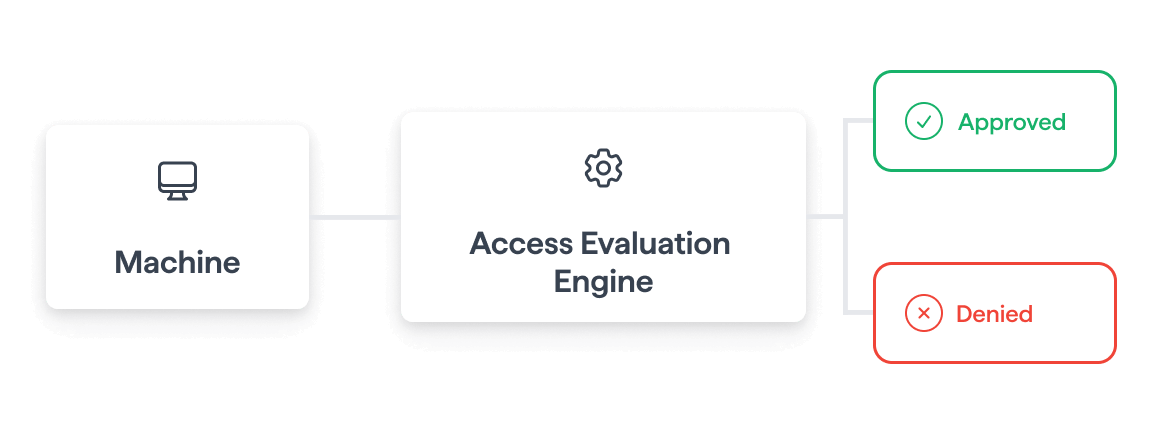
Control how apps connect
Keep applications secure by limiting what they can access, with Machine-to-Machine (M2M) Controls.
- Define what external services can access through your apps.
- Keep applications and human users separate, for added security.
- Give apps only the permissions they need, to reduce risk.

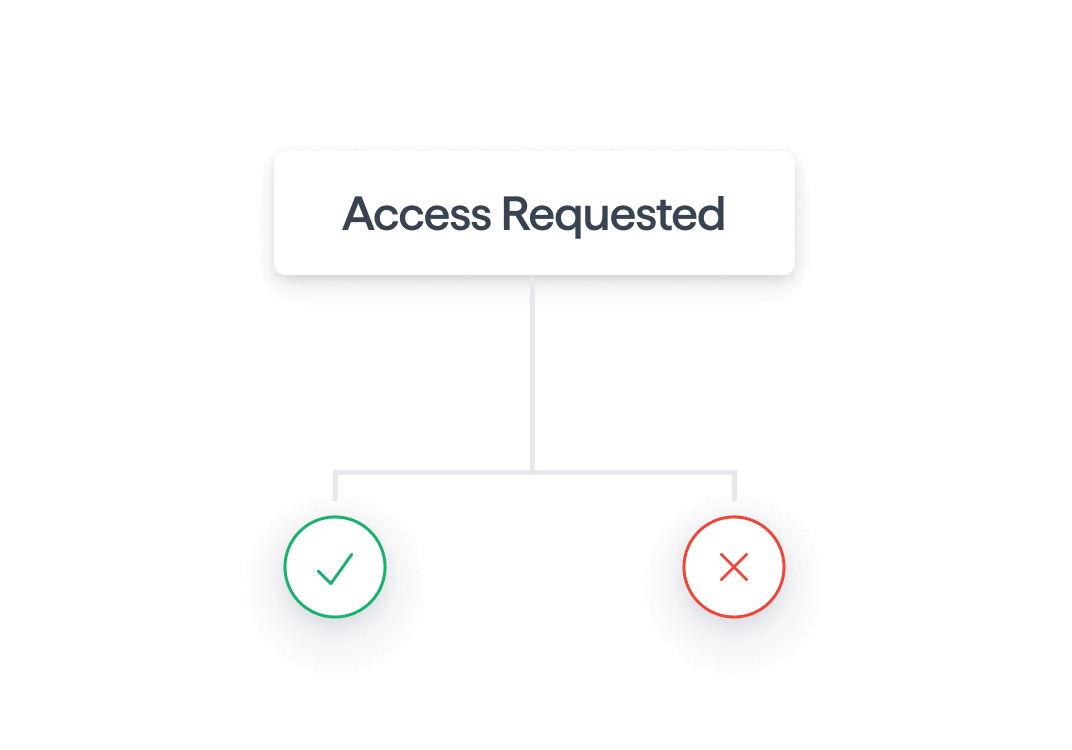
Review access requests
Get and review user access requests for products and data in your organization.
- Easily manage user access requests from your users and customers.
- Review requests directly on our platform to give a smooth experience for customers and users
- Quickly respond to changing user needs
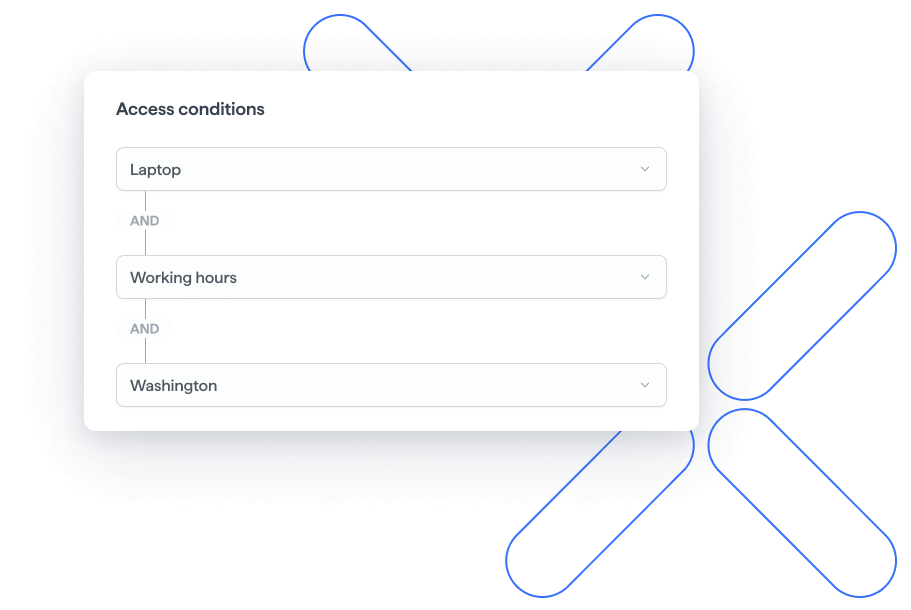
Adjust access based on context
Check location, time, or device to make access more secure, with Contextual Access Control.
- Check location, time and device for added security.
- Adjust permissions based on context to avoid unauthorized access.
- Reduce the risk of data breaches or mistakes.
- Keep your system more flexible with access decisions that fit each situation.

.webp?width=839&height=740&name=Vector%20(9).webp)
